
What do I mean when talking about “Online Privacy?” The best definition I’ve encountered is the three-part description by Eben Moglen, founder of the Software Freedom Law Center, in his lecture series titled “Snowden and the Future” in 2013 at Columbia Law School:
Privacy - as we use the word in our conversations now all around the world, and particularly when we talk about the net - really means three things:
The first is Secrecy, which is our ability to keep messages "private" so that their content is known only to those who we intend to receive them.
The second is Anonymity, which is our ability to keep our messages - even when their content is open - obscure as to who has published them and who is receiving them. It is very important that anonymity is an interest we can have in both our publishing and our reading.
The third is Autonomy, which is our ability to make our life decisions free of any force which has violated our secrecy or our anonymity.
These three are the principle components of the mixture that we call "privacy". With respect to each, further consideration shows that it is a precondition to the order that we call "democracy", "ordered liberty", "self-government", to the particular scheme that we call in the United States "constitutional freedom".
A complete transcript of Mr. Moglen’s four-part lecture on the topic can be found HERE.
ProtonMail also has a great blog post explaining the distinctions between security vs. privacy vs. anonymity,
Another great resource is the Electronic Freedom Foundation (EFF), an independent non-profit working to protect peoples’ online privacy for nearly thirty years. EFF states on its web site Privacy page:
“New technologies are radically advancing our freedoms, but they are also enabling unparalleled invasions of privacy. National and international laws have yet to catch up with the evolving need for privacy that comes with new digital technologies. Respect for individuals' autonomy, anonymous speech, and the right to free association must be balanced against legitimate concerns like law enforcement.”
Where did it go?
The moment you connect your computer or mobile device to the Internet, even before you open your browser, you become at risk to surveillance and tracking by the government and other third parties. When you launch a web browser or other web-based app, you become vulnerable to everyone else in the world, especially if you use social media. It is more important than ever to protect your privacy rights. Governments and corporations like Google, Facebook, Amazon, Twitter, DoubleClick,  AddThis, sophisticated hacking groups, and many others have been totally disregarding people’s privacy rights throughout the world. This especially true for the social networking, advertising, and web site analytics entities (like Cambridge Analytics). These entities are tracking your every move and location, both online and actual physical location through the combined use of online activity trackers and data analytics, coupled with real-time GPS data.
AddThis, sophisticated hacking groups, and many others have been totally disregarding people’s privacy rights throughout the world. This especially true for the social networking, advertising, and web site analytics entities (like Cambridge Analytics). These entities are tracking your every move and location, both online and actual physical location through the combined use of online activity trackers and data analytics, coupled with real-time GPS data.
Cookies, super cookies, flash cookies, bugs, beacons and a variety of third party elements (TPE) can be used to determine your IP address and then be cross-referenced and linked to your email address(es), social media profiles and other accounts.
All of this collected data is stored indefinitely in massive database repositories that are mined to create ever-more detailed unique personalized user profiles. These unique profiles are used to identify and track what you buy, where you go, what you like/don’t like, who you communicate with, what devices you use, what browser you use, the apps you use, and much more. This data is used to define who these companies think you are. They follow your wanderings around the Internet, they insert user-specific ads on the web pages you visit, and monitor your online activity a minute-to-minute basis. Often, software provided by these companies include undisclosed capabilities specifically designed to extend a their ability to remotely observe, influence, and to some extent control your online behavior.
I don’t know about you, but I find this all very intrusive and quite unsettling.
Privacy & security trends
Global Surveillance – mass surveillance technology continues to strengthen and expand around the world – particularly in the United States, United Kingdom, Australia, and other Western countries. (See also the Five Eyes, Nine Eyes & 14 Eyes surveillance alliances.) This trend continues on, regardless of which political party is in office.
ISP Spying – Internet providers often record connection times, metadata, and DNS requests, which gives them every website you visit (unless you’re using a good VPN). In many countries, this is not only legal, but required. See for example in the United Kingdom (with the Investigatory Powers Act), United States (Senate Joint Resolution 34), and  now also in Australia (mandatory data retention). A VPN is now essential protection against your internet provider if you want to retain a basic level of online privacy.
now also in Australia (mandatory data retention). A VPN is now essential protection against your internet provider if you want to retain a basic level of online privacy.
Censorship – The internet is also becoming less free due to censorship efforts and content blocking. Whether it is China, Germany, or the United Kingdom, authorities are working hard to censor content online. This is particularly the case in Europe. The UK is now considering 15 year jail sentences for people who view “offensive” websites.
Profiling, Malicious Ads & Tracking – Websites are increasingly hosting invasive advertisements that also function as tracking tools. Pop-ups and dangerous “click-bait” ads can also deliver malware and take your device over for ransom (ransomware). Malicious ads (malvertising) delivered through third party ad networks trick users into downloading, can even be hosted on major websites. While cookies are still used to track your online behavior, the technology called “fingerprinting” leverages the ability to interrogate your network devices to identify elements unique to your technology and online behavior to track your browsing activity across the web without cookies.
There is well-founded concern that governments, employers, insurance companies, unscrupulous retailers, financial institutions, and any third party are also collecting and mining this highly personal information with total disregard for your privacy rights. For example, they can build a detailed profile of you, which may or not be accurate, and use it to determine:
• If you represent a subversive risk to your government
• If you might pose a risk for drug or alcohol abuse or whether you  may not be quite the “right fit” for a potential employer whether you qualify for a loan or insurance coverage
may not be quite the “right fit” for a potential employer whether you qualify for a loan or insurance coverage
• What variable price you are charged for goods or services (different prices being displayed to different people for the same products or services)
• Whether you should be accepted as a member to a club or society
• Whether you are a suitable match for a potential mate
• Your suitability as a potential tenant or renter
Our profiles and the data used to build them are becoming a substitute for blood, urine, and genetic testing. But, unlike the tightly regulated testing of these substances, the how, where, and by whom your online profile is used is the Wild West - Anything Goes. And you are being watched. Private and government-sponsored organizations are monitoring and recording all of your online activities. Read the article on the EFF web site entitled “Behind the On-Way Mirror: A Deep Dive into the Technology of Corporate Surveillance” for an in-depth look at how corporations are monitoring and tracking your online activity.
An example is the alarming trend of employers asking job candidates for their social media passwords. Currently this takes the form of the potential employer asking for the password directly and poking around your social media account or by asking the job candidate to login with the scrutinizing employer taking a look.
From a privacy perspective, it’s important to block ads because they function as trackers by recording your online activity to create an intimate user profile, which is used for targeted ads. Ads are also risky from a security perspective because they are often malicious and can infect your device when a web page loads – no clicks required. 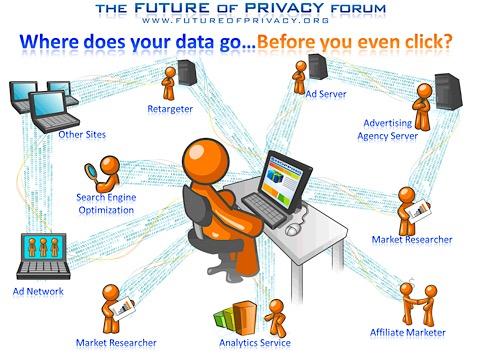
Add it all up and the trackers and profilers can follow you across all your devices all the time, anywhere, and they don’t have to rely solely on your IP address.
This means that choosing and implementing a strong set of online privacy and security tools is now more important than ever. How much privacy and security do you need given your unique situation?
Everyday internet surfers are seeking protection against online tracking online through advertising networks, as well as identity theft protection and a higher level of online anonymity and security. Others, such as investigative journalists working with sensitive information are looking for an even higher level of protection.
Additionally, many web sites have begun using location data to offer regional specific services and serve targeted advertisements. Mapping applications have legitimate reasons for gathering location data, but that same technique can be used to help identify who you are. A good browser should let you toggle on and off location data – for security and privacy you should leaving it off completely. At the very least, demand that websites prompt you for access before gathering the data. Also, IP-based geolocation data is incredibly trivial to acquire, so remain vigilant. If you're browsing the Web without a proxy or a VPN (discussed below), you're effectively broadcasting your IP address to every server you come across, and that information can be used against you. It's also good this in the back of your mind if you're criticizing your local dictator or blowing a whistle on the company you work for or on the NSA.
What follows is a set of great resources if you want to take control of your online privacy and security.
Hide your tracks — Regain your privacy
Good privacy is all about layering – no single tool exists that provides a comprehensive solution to privacy. You need to build a multi-layer complementary approach that starts with your browser. Everyone needs to be using a secure and privacy-friendly browser and Internet connection services for these important reasons:
• Browsers can be compromised in many ways.
• Browsers contain lots of private information about you.
• Companies can read, retrieve, record, monitor, and store detailed information about your computer and browsing habits.
• ISPs can track and record all unencrypted content you send and receive when connected to their network servers.
• Google, Amazon, Yahoo, etc. can all track and record all search activity performed using their search tools.
• Search requests are sent thru unencrypted DNS servers that route your search to correct web sites.
• All of this data can be used to identify and track you through browser fingerprinting and profiling.
To see how you are tracked by your IP address, go to https://www.cogipas.com/whats-my-ip/. The sites listed there demonstrate what is just the tip of the iceberg about the kind of hidden information that your web browsing activities reveal. Increasingly, your online digital fingerprint is being determined by other factors too. This Consumer Reports web page has a great checklist of 66 things to do to improve your online security and privacy that include many actions not covered by my site.
The EFF Surveillance Self-Defense web page is an expert guide to protecting you and your friends from online spying.
The web site, privacytools.io provides services, tools and knowledge to protect your privacy against global mass surveillance.
The following graphic offers a glimpse as to how companies track internet users.
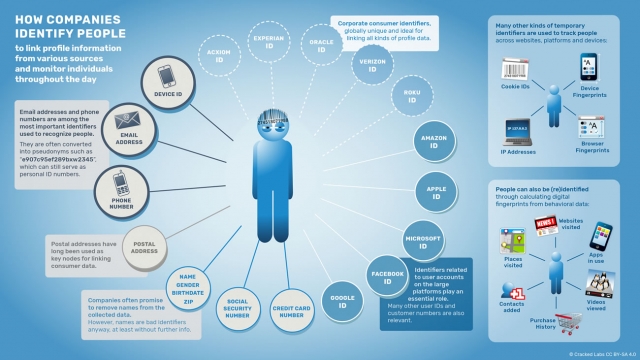
If your really value your privacy, your should eliminate use of all Google products. All products made by Google, and parent company Alphabet, are designed and built to monitor, track, collect, record, store, analyze, and monetize every user’s personal data, regardless of its type. This includes Google Search, Google Docs, gmail, Google Maps, Google Earth, Android OS, AdSense, Analytics, and many more. For a more detailed list of Google products, check out the following Wikipedia web page: https://about.google/intl/en_us/products/?tip=automatic-photo-backup
To reclaim and protect your privacy, take the following steps to build a strong online defense perimeter
2. Next Install Browser Add-ons
3. Switch to a Private Search Engine
4. Thwart Search Engine Tracking URLs
5. Additional Ad Blocking Steps for Hiding Your Tracks
6. Subscribe to a Virtual Private Network (VPN) Service
8. Test to Assess Your Security / Privacy
1. Use a Browser that Respects Your Privacy
By default, most browsers will contain lots of private information unique to you, including your browser type, browsing history, usernames, passwords, geographical location, IP address, computer type, operating system, and configuration, auto-fill information (such as your name, address, etc.). All of this data can be collected, updated, stored in massive databases, and constantly analyzed to identify and track not only your online browsing activity, but also purchase preferences, physical location, geographic travel patterns.
Here are some great options for selecting a secure, privacy focused browser.
Firefox – Firefox is a great browser for both privacy and security. It is highly customizable to give you the level of security and privacy you desire, while also being compatible with many browser extensions.
Waterfox – Waterfox is a fork of Firefox, with telemetry and other items stripped out to give users more privacy. It is based on Firefox 56 with ESR patches.
Tor – The Tor browser is hardened version of Firefox that also utilizes the Tor network by default (but this can be disabled). It should be noted that Tor was created by the US military and continues to be funded by the US government today. (See the in-depth Tor guide for more details.)
Brave – Brave is based upon Chromium (the open-source version of Google Chrome) that has been modified to provide a privacy-focused browser right out of the box. By default, it will block ads and trackers, and it’s also customizable, fast, and has built-in protection against browser fingerprinting.
Do not use the following popular browsers if you have privacy concerns:
Google Chrome – It offers good security, but it is extremely invasive and collects all kinds of private data, which Google uses for targeted ads.
Opera – This browser technology was acquired by a Chinese company that has a troubling privacy policy regarding data collection and sharing practices. Plus, all Chinese company’s operations and technology products are closely monitored by Chinese government, which raises red flags concerning security and privacy compromise through spying on and monitoring of user activity.
Microsoft Internet Explorer (IE) – This browser is riddled with security and privacy holes (such as ActiveX) that are constantly being exploited and compromised by hackers and can lacks user configurable parameters to limit privacy tracking technology.
Microsoft Edge browser – this new browser does offer more security than IE, since it’s based on open-source Chromium code base. However, it seriously compromises user privacy, since it uses proprietary extensions, many unclear settings, and a lot of data collection enabled by default.
Harden your browser by installing a combination of the following add-ons – these tools extend the privacy and security abilities of Firefox, Chrome, Chromium, and Opera turning them into secure browsing platforms. Note that add-ons built to integrate with Firefox can also added to other browsers based upon Firefox. Online ads may still be using up resources and tracking you, even if the ads are not being displayed. Choose an ad blocker carefully – some ad blockers, such as Ghostery and Adblock Plus will collect user data for profit and/or show you “approved” ads. By far, Firefox offers the most comprehensive set of privacy and security extensions. Here are a few that I use:
HTTPS Everywhere – In spite of some infamous security issues, SSL is still extremely important for keeping your Web traffic safe from prying eyes. If you want to keep nosy packet sniffers out of your business, your Web traffic should always be going through SSL connections. Sadly, not every website supports SSL. Even worse, many websites that do support SSL still default to unencrypted connections -- and the Electronic Frontier Foundation (EFF) wants to change that. The HTTPS Everywhere browser extension, provided for free by the EFF, forces SSL connections on countless websites. Chrome, Firefox, and Opera users can all take advantage of this wonderful extension, and keep important Web traffic private and secure.
Privacy Badger – EFF's Privacy Badger add-on. Available for Chrome, Firefox, and Opera, this browser extension monitors when sites try to track your browsing habits, and automatically thwarts future tracking attempts. The list of blocked content automatically improves as you browse -- no need to manually block trackers.  Better yet, you can configure this add-on to disable WebRTC tracking as well.
Better yet, you can configure this add-on to disable WebRTC tracking as well.
Decentraleyes – A web browser extension that emulates Content Delivery Networks (CDN) to improve your online privacy. It intercepts and blocks incoming traffic from third-party servers, finds supported resources locally, then substitutes and injects them into your browser environment. All of this happens automatically, so no prior configuration is required.
Cookie AutoDelete – Add a tool like Cookie Autodelete that can easily manage and delete pervasive cookies or set your browser to delete all cookies when exiting the browser.
NoScript – This add-on is a JavaScript blocker providing in-depth control over scripts that run on the sites you visit. JavaScript is incredibly powerful, but that useful little scripting language can be used against you. By design, it can deliver detailed information about your system to any Web server. What plug-ins do you have enabled? What size screen are you using? Those small pieces of information can add up, and make tracking your usage profile easier for advertisers and governments. Worse, unpatched JavaScript exploits could potentially be used to trick your browser into giving up even more identifying information. If you want to be truly anonymous, you're going to need to disable JavaScript. That's easier said than done, since many websites rely on JavaScript for core functionality, so you'd be effectively knee-capping your Web browser. But when you use extensions like NoScript, you can manually manage which domains have permission to run JavaScript in your browser. This way, you can whitelist only the domains and webpages that you absolutely trust.
uBlock Origin – A powerful blocker for advertisements and tracking.
uMatrix – While this may be overkill for many users, this powerful add-on gives you control over requests that may be tracking you on various websites. If you use this, you will not need uBlock Origin.
Trace – An advanced extension that can protect many different types of browser fingerprinting such as Canvas/Audio/WebGL Fingerprinting. Trace also offers URL cleaning and header editing features such as the tracking cookie eater and Google header remover.
Disconnect for Facebook – This add-on provides a firewall to prevent Facebook from tracking the webpages you go to by blocking all Facebook related requests sent from all third-party websites, while still allowing you to visit your Facebook account with no problem. It has a very low memory and CPU footprint and can be easily toggled on and off from the toolbar button.
Skip Redirect – Some web pages use intermediary pages before redirecting to a final page. This add-on tries to extract the target URL from the intermediary URL and goes there straight away if successful.
Canvas Blocker – This add-on allows users to prevent websites from using some Javascript APIs to fingerprint them. Users can choose to block the APIs entirely on some or all websites (which may break some websites) or fake its fingerprinting-friendly readout AP.
Decentraleyes – This one protects you against tracking through "free", centralized, content delivery. It prevents a lot of requests from reaching networks like Google Hosted Libraries, and serves local files to keep sites from breaking. Complements regular content blockers. Many web sites are now using third-party CDN (content delivery network) services. CDN providers profit either from direct fees paid by content providers using their network, or profit from the user analytics and tracking data collected as their scripts are being loaded onto customer's websites inside their browser origin. As such these services are being pointed out as potential privacy intrusion for the purpose of behavioral targeting[6] and solutions are being created to restore single-origin serving and caching of resources
3. Switch to a Private Search Engine
It’s no secret that big search engines (Google, Yahoo, Bing) record and track everything you do related to your searches. This includes tracking the sites you visit after leaving their search page, which helps them to build unique user profiles for their advertising partners.
However, there are really great alternatives to “the usual suspects” that take user privacy seriously and do not record or track any of your search activity.
DuckDuckGo.com – This is a great privacy-friendly Google alternative that doesn’t utilize tracking or targeted ads. They also have a zero-sharing policy, but they do record search terms. DuckDuckGo utilizes the Bing search platform but strips all tracking and profiling code from before returning your search results.
StartPage.com – StartPage gives you Google search results, but without the tracking. It was created in 2004 as "the world’s most private search engine", which doesn’t log, track or share your personal data. It has added many additional privacy features, like " Anonymous View " for further protection. Startpage.com is privately held by Startpage BV, an EU-based company, where privacy laws are amongst the most stringent in the world.
searX.me – This search engine is a very privacy-friendly and versatile metasearch engine that queries and returns search results from over 70 Internet search databases. It uses HTTPS/SSL. It’s code is 100% open source available for review by anyone. searX.me does not share users' IP addresses or search history with the search engines from which it gathers results. Tracking cookies served by the search engines are blocked, preventing user-profiling-based results modification. By default, searx queries are submitted using a protocol that prevents users' query keywords from appearing in webserver logs.
Qwant.com – A private search engine based in France. Qwant philosophy is based on two principles: no user tracking and no filter bubble. Qwant was launched in France in February 2013.
MetaGer.org – Is a meta search engine quering up to 50 search engines offering real variety in results based on relevancy – not by “filter-bubble,” user profile, “fingerprint” identity, or search engine optimization algorithm. It’s a non-profit, charitable association committed to transparency and free access to knowledge for all. It understands free research is not compatible with mass surveillance and takes privacy very seriously. As such, MetaGer always only processes data that is necessary for the operation of our services. It does not log, track, record, share, or profile any user’s of its search engine - it doesn’t store or share user IP-addresses, user-agent data, search queries, or location data. All user searches are performed anonymously, including route-planning and geographical / mapping data via anonymous proxy and the Hidden-Tor-Branch. It has its own anonymizing geo-mapping service, maps.metager.de, to ensure this privacy. It uses open-source software allowing 3rd-party examination and verification checks. MetaGer uses green electricity for our servers. It also clearly explains what and how it handles user data essential for processing a user’s search requests.
Swisscows.com – They do not collect your data, track, or store your data. Swisscows provides complete search anonymity. They own all of their own servers and do not work with a cloud or third party. Their data center is in a secured bunker the Swiss Alps and have positioned everything geographically outside of EU and US.
searchencrypt.com – All user searches are encrypted. Search Encrypt does not track user's searches or search history. They also claim to make use of the newest and best possible security features, including Perfect Secrecy SSL to protect user's searches and ensure that they remain private.
Yippy.com – Yippy is committed to respecting and protecting the privacy of the users of its services. No personally identifiable information is ever required, since Yippy is intended to be an anonymous service. IT does collect limited session-based non-personally identifying information that your browser makes available, to deliver its search services, including your IP address, browser type & language, referral data, date and time of your query, and one or more cookies (described below) that may uniquely identify your browser, which are deleted when your session ends — cookies are not used to uniquely identify you or track your behavior. You can set your browser to refuse all cookies and still use Yippy search services. Yippy doesn’t sell or provide personally identifiable information to any third parties, nor does it provide advertising or third party tracking scripts.
4. Thwart Search Engine Tracking URLs
It's no secret that Google makes money by tracking your behavior for targeted ads, and that's problematic from a privacy perspective. Using DuckDuckGo is a good alternative for some of us, but the quality of Google's results can be difficult to forgo. Thankfully, you can easily sidestep one of Google's most obnoxious behaviors: URL trackers. When you click on a URL in Google, it actually loads a redirect URL first for easier tracking. Even worse, simply copying the link from Google can give you a long, messy tracking link instead of the plain URL you really want.
Searchlinkfix for Firefox – This is a Firefox-only add-on that completely strips away the tracking string that Google attaches to each web link you click on the Google search results page. This extension prevents Google and Yandex search pages from modifying search result links when you click them. This is useful when copying links but it also helps privacy by preventing the search engines from recording your clicks.
Searchlinkfix for Chrome - This is the link for Chrome-only add-on by the same developer of the Firefox add-on.
Searchlinkfix for Opera - This is the link for the Opera-only version of the add-on
5. Additional Ad Blocking Steps for Hiding Your Tracks
To obtain and maintain maximum privacy, you need to effectively block all ads served up to your browser as you surf the Internet. Note that ad-blocking works differently on mobile devices, especially on iPhones and iPads, where there aren’t as many options. The best ad blocking setup will depend on your situation and needs. If you have numerous devices you use at home, setting up a network-wide ad blocker would be a good solution for blanket protection.
Here are a few different options to help you achieve better privacy.
Dedicated Ad blocker apps – A dedicated app will most likely do a very good job blocking ads on your device. One popular and well-regarded option is AdGuard.
VPN Ad blocker – Another option is to use a VPN service that offers an ad blocking feature (VPN ad blocker), such as ProtonVPN, Perfect Privacy VPN and IPVanish VPN service.
Ad blocking on a router – Ad blocking on a router can be accomplished various ways – from using ad blocking DNS to loading custom filter lists onto your router.
Block Location Data – Any proper browser should let you toggle on and off location data and I recommend leaving it off completely or at least until you really need to find something. At the very least, demand that websites prompt you for access before gathering the data. That said, IP-based geolocation data is incredibly trivial to acquire, so remain vigilant. This is especially relevant if your mobile phone or tablet is connected to cellular service or WiFi hotspots. If you're browsing the Internet without a proxy or a VPN, you're effectively broadcasting your IP to every server you come across, and that information can be used to determine where you are located.
6. Subscribe to a Virtual Private Network (VPN) Service
Using a VPN (virtual private network) is one of the simplest and most effective ways to protect your privacy, secure your devices, and also access blocked/censored content online. A VPN creates an encrypted tunnel between your device and the VPN server that substitutes your actual IP address with one assigned by the VPN server that . 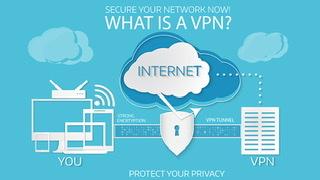 The VPN server-assigned IP address becomes the IP address that all Internet site that you visit during your connection time. This masks / hides your actual IP address from any web sites you visit giving you a degree of privacy and security.
The VPN server-assigned IP address becomes the IP address that all Internet site that you visit during your connection time. This masks / hides your actual IP address from any web sites you visit giving you a degree of privacy and security.
There are many reliable, reputable VPN service providers spread throughout the world. As such, it is important to know where the provider’s business offices are located for legal jurisdiction purposes, since legal protection for digital data privacy rights vary greatly from country to country. All VPN providers offer a range of services with varying levels of privacy and security protections, so it is important to determine your privacy and security needs when selecting a VPN service provider.
But beware of VPN providers offering “Free!” services – while some are legitimate responsible businesses (like ProtonVPN), many free VPN providers often collect and sell user data, have very few servers, offer limited bandwidth, and collect/maintain extensive logs of user activity – some are outright scams and various marketing gimmicks.
The best providers are ones who openly and clearly spell out their subscriber privacy commitments, such as no logging of user activity, encryption of all records, policy on disclosing logs to law enforcement, etc.
VPNs can range in price from $2.99 per month (NordVPN) up to $12.99 per month (Perfect Privacy) . When you purchase a VPN subscription you will be able to use the VPN on various operating systems and devices, from computers and tablets to phones and routers.
If you're serious about maintaining your anonymity, consider investing in a VPN solution like ProtonVPN, TorGuard, or Private Internet Access. While the protection isn't perfect, they will help you to disguise your activities online. Your real IP address will be hidden from the world, and your traffic will remain indecipherable to nosy ISPs or governments. Even if your country is actively on the lookout for VPN traffic, you can still benefit from so-called "stealth VPNs." TorGuard offers its stealth VPN service at no additional cost, and it will make government detection and interference much harder to accomplish. For those of you being held hostage by your government, VPNs are by far the best bet for bypassing censorship and snooping.
Note that the “best VPN” solution will differ for each person based on unique needs, service cost, bandwidth requirements, and privacy circumstances. For an in-depth overview of all the different VPN router options, see this VPN router guide.
If you are tech savvy, a less expensive way to secure your entire home network and all devices, is to use a router (either WiFi or hardwired) that incorporates firewall and VPN capabilities. A good VPN router will:
Extend the benefits of a VPN to all your devices without installing software
Protect you against mass surveillance and internet service provider (ISP) spying
Secure your home network against attacks, hacking, and spying
Unlock the entire internet, allowing you to skirt geographic restrictions, blocks, and censorship
The only reasonably priced consumer brand currently offering a large selection VPN-enabled routers is Asus. The default Asus firmware, which is called ASUSWRT, supports OpenVPN, PPTP, and L2TP right out of the box (no flashing required). The Asus RT-AC68U is an excellent choice.
There are numerous brands offering business-grade routers that incorporate both firewall, router, and VPN capability, but these can be quite costly, especially if you by a support subscription. They are usually more complex to set up and manage. The Fortinet FortiGate E30 and WatchGuard Firebox T15 two good options if you want this increased degree of protection.
When choosing a router, the biggest consideration is processing power (CPU). Running a VPN on a router is a very CPU-intensive task requiring the router to process lots of encrypted data. For these reasons, it’s typically good to go with a router that’s at least 800 Mhz or more.
Beware: choosing this solution makes you responsible for all maintenance — this includes updating router/VPN software security updates, setting up strong password policies, setting security intrusion alerts and reviewing the logs, etc. So while it may be lower cost than a VPN service subscription fee, it will require more of your time to keep the VPN service secure and protected.
8. Test Your Privacy / Security
It isn’t enough to install / implement the various recommendations and then forget about it. It’s also important to test and verify that the privacy and security tools you implemented are delivering the desired protections. I’ve provided some info and links below to help you conduct an extensive test of your browser privacy and security posture.
BrowserLeaks.com – This site is all about Web Browser Fingerprinting. Here you will find the gallery of web browser security testing tools that tell you precisely what personal identity data may be leaked thru your browser without any permissions when you surf the Internet. This toolset will never be completely exhaustive, but this site is an invaluable asset to can help you determine that your privacy and security precautions are really working. You should also use this tool any time you make configuration changes to your browser or computer systems. Currently, BrowserLeaks provides the ability to run and report on your browser leak exposure status of the following data:
IP Address - Main tool that illustrates server-side abilities to expose the user identity. It contains a basic features, such as Showing Your IP Address and HTTP Request Headers. As well as Proxy Detection in all possible XFF headers. GeoIP Data Acquisition about the general IP Address and all of a Proxy IP's (Country, State, City, ISP/ASN, Local Time, Latitude/Longitude), and put all IP places to the Map. In addition, here is a special features — Passive TCP/IP stack OS Fingerprinting, DNS and WebRTC Leak Tests.
Java Script status - A lot of user data can be obtained using common JavaScript functionality. DOM Window Object disclose much of sensitive information about the web ![]() browser: User-Agent, Architecture, OS Language, System Time, Screen Resolution. There is a listing of the NPAPI Plug-ins and Windows Explorer Components. Also there is already implemented: detection and obtaining data through a brand new HTML5 API's, such as the Battery Status API and Navigation Timing API.
browser: User-Agent, Architecture, OS Language, System Time, Screen Resolution. There is a listing of the NPAPI Plug-ins and Windows Explorer Components. Also there is already implemented: detection and obtaining data through a brand new HTML5 API's, such as the Battery Status API and Navigation Timing API.
Flash Player - Describes the Flash Player Runtime properties that can be provided through the use of AS3 System Capabilities: Flash Version, Plugin Type, Operating System, Manufacturer, System Language, Web Browser Architecture, Screen Resolution, and many other properties that describe the hardware and multimedia capabilities of the system.
Silverlight - Getting system information using Silverlight Plug-In, installed in your web browser. Shows your system environment details such as: OS Version, Processor Count, System Uptime, Time Zone, Installed Fonts, System and User Culture, Region and Language OS settings, as well as part of evercookie to test Silverlight Isolated Storag Cookies.
Java Applet - What kind of permissions usual unsigned Java Applet has? It can be the extended Java Machine description, OS Detection: Name, Version, Arch, User Locale, and some file system related information. CPU Cores count, amount of Dedicated Memory, JVM instance Uptime, Network Interfaces Enumeration.
WebGL - Web Graphics Library Browser Report checks WebGL support in your browser, produce WebGL Fingerprinting, shows other WebGL and GPU capabilities more or less related web browser identity. Also this page contains the How-To enable or disable WebGL in a modern web browsers.
WebRTC - Web Real Time Communications is used to facilitate real-time data stream between your browser and a web server. A user’s IP address is required to help establish this path and your browser. The fundamental vulnerability with WebRTC is that your true IP address can be exposed via STUN API requests with Firefox, Chrome, Opera and Brave, Safari, and Chromium-based browsers, even when you are using a good VPN. Nefarious websites could potentially use this information to fingerprint individuals who do not want to be tracked.
Canvas Fingerprinting - Browser Fingerprinting without any of user agent identifiers, only through HTML5 Canvas element. The method is based on the fact that the same canvas-code can produce different pixels on a different web browsers, depending on the system on which it was executed.
Font Fingerprinting – This tracking method is based upon the composite unique characteristics of all fonts you have installed and how your browser renders these fonts. This technique measures the dimensions of the filled with text HTML elements, it is possible to build an identifier that can be used to track the same browser over time. A unique font fingerprint is one of the easiest ways to track a user and is difficult to effectively defend.
Content Filters - The set of demos that try to determine Content Filters usage, is the type of applications that operate between the browser and the web page, and are designed to manipulate the connection and content of a visited web pages. Among them are Tor Browser, Privoxy, Adblock Detectors.
Geolocation API - Tool for testing HTML5 Geolocation API. Checking the browser's permissions to geolocation. Based on the latitude longitude and accuracy received from the browser, shows the possible radius of your location on the interactive map.
Browser Features Detection - Web Browser's Features Detection via Modernizr — library that detects HTML5 features. It once again shows how powerfully modern JavaScript affects to web browser's identity. This tool is also used by web developers (as "Modernizr Helper") for quickly testing web browsers’ compatibility with HTML5 features.
DNS Leak Testing – Even if you use a privacy service like a VPN, it's still possible to give away clues to your identity via your DNS traffic. Thankfully, it's easy to detect if your configuration is leaking your DNS information. Simply head over to DNSLeakTest.com, and run the extended test. If the results show the third-party DNS service you're using (like TorGuard), you're set. If your ISP's DNS info shows up, you have a DNS leak. Follow the steps listed on the "How to fix a DNS leak" page, and then test yourself again to make sure everything is working as intended.
Avast Safer.com - This site provides the ability to run a subset tests that checks for the most common set of browser leaks and provides the results in one consolidated online report. This report is a bit easier to understand.
Who’s Tracking You – Use the decentraleyes.org/test testing utility to find out if you are properly protected against online tracking by 3rd-party content delivery networks (CDNs). (Note: does not work with Apple iOS)
Lightbeam – Lightbeam is a browser extension that uses interactive visualizations to show you the interconnecting relationships between the multiple tracking sites and the sites you visit. (Note: Does not work with Apple iOS)
Panopticlick - This site, provided by EFF, tests how well protected you are against non-consensual Web tracking. This tool analyzes and reports on the following five browser vulnerabilities:
1. Does your browser block tracking ads?
2. Does your browser block invisible trackers?
3. Does your blocker stop trackers that are included in the so-called “acceptable ads” whitelist?
4. Does your browser protect from fingerprinting?
5. Does your browser unblock 3rd parties that promise to honor Do Not Track?
9. Additional References and Resources
Follow this link to my web page containing links to other great resources and reference sites that I use to keep current with the developments in online privacy and security.
