What is a Password?
I use the metaphor of a password as a unique “virtual key” used to unlock a specific virtual room within a large building where I store items of valuable. Using this metaphor, we usually have a different unique key to access each locked room - no two room locks use the same key. Extending this analogy, if you use the same key for all of the locks on your virtual rooms, you’re created a master key. As such, if anyone were to steal or copy your master key, they would have free access to all of your personal and financial data.
where I store items of valuable. Using this metaphor, we usually have a different unique key to access each locked room - no two room locks use the same key. Extending this analogy, if you use the same key for all of the locks on your virtual rooms, you’re created a master key. As such, if anyone were to steal or copy your master key, they would have free access to all of your personal and financial data.
Have I Been Pwned (HIBP) is a web site created by Troy Hunt as a free resource for anyone to quickly assess if any of a user’s online accounts may have been put at risk due in a data breach. Pwned (“poned”), a slang term derived from the verb own, refers to user data, including log-on credentials, that was appropriated, hacked, stolen, or compromised through a security breach of a company’s server(s). Click here to check if any of your log-on credentials have been exposed in a data breach.
What makes a good password?
Every password can be defeated given sufficient time & resources. And with the ever evolving processing power and speed of modern computers, the timeframe for defeating passwords continues to shrink. Just a few years ago, 8-alphanumeric passwords used to sufficient- now a strong password must be at least 12-characters, composed of alphanumeric and special ASCIl symbols. And the simple password is itself no longer recommended. Now it’s recommended that users create unique “passphrases” comprised of 3 to 4 easy-to-remember words not normally found together. You need to identify how strong your passwords need to be to protect your data from cyber criminals and other adversaries.
Password strength is measured in degree of entropy (randomness in a pattern) which  represents the maximum number of guesses a brute-force method would require to guess a given password, based upon an estimated number of trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. A brute-force method is a computing algorithm that tests a large number of keyboard character combinations in the effort to find a password pattern match. The strength (entropy) of a password is a function of length, complexity, and unpredictability.
represents the maximum number of guesses a brute-force method would require to guess a given password, based upon an estimated number of trials an attacker who does not have direct access to the password would need, on average, to guess it correctly. A brute-force method is a computing algorithm that tests a large number of keyboard character combinations in the effort to find a password pattern match. The strength (entropy) of a password is a function of length, complexity, and unpredictability.
It is relatively easy to create strong passwords - the challenge is striking the right balance of complexity and usability so one can easily remember and use their passwords when needed. The following Wikipedia page provides a good explanation of password strength and how it’s calculated, if you would like more detailed information: https://en.m.wikipedia.org/wiki/Password_strength
Strong Passwords
Guidelines for choosing good passwords are typically designed to make passwords harder to discover by intelligent guessing. Your password is your “key” for accessing private resources on the ‘Net. And a key is what we use to keep our data secure when connected the ‘Net. It is recommended to use different passwords for different websites but you better make sure that the password you are using is hard to guess or hard to crack.
Utilize the following password management best practices to make sure you have strong, secure passwords:
-
- Most important - use a minimum password length of 12 or more characters, if permitted by log-in parameters.
- Never use words that are very common and short: admin, strong, love, black, password, or words from a dictionary, etc.
- Avoid using personal information as your password, like people’s names,
 dates of birth, social security number, favorite animal’s name.
dates of birth, social security number, favorite animal’s name. - Your password should never contain your user name, real name, or your company’s name.
- Avoid using the same password twice (e.g., across multiple user accounts and/or software systems).
- Avoid character repetition, keyboard patterns, dictionary words, letter or number sequences, usernames, relative or pet names, romantic links (current or past) and biographical information (e.g., ID numbers, ancestors' names or dates).
- Use special characters in your password where permitted, such as: @!+(= and a combination of upper and lower case letters and numbers. Note that the allowable character set may be constrained by a web site or
- Make sure that your new password is different from all the previous ones you made up.
- Avoid using information that is or might become publicly associated with the user or the account.
- Avoid using information that your colleagues and/or acquaintances might know to be associated with you.
- Do not use passwords which consist wholly of any simple combination of the aforementioned weak components.
- Do not use any single taken from a dictionary - hackers actually use dictionary databases for brute-force password cracking.
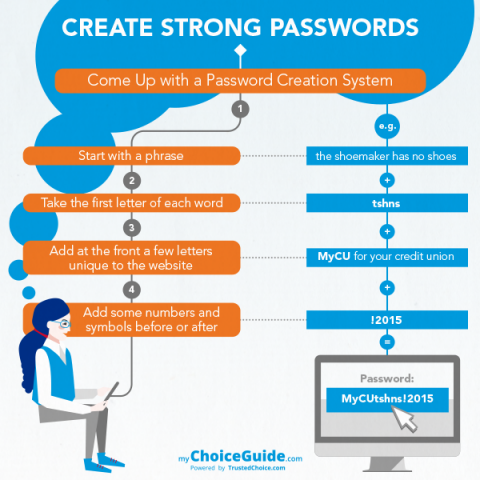
- Use an easily-memorized phrase or short sentence, combined with numbers and upper/lower case letters e.g., You1Can’t2Crack3This4 (!do not use this password!)
- Use two-factor authentication (2FA) whenever possible to log in to websites containing your or your family’s banking, investments, credit cards, healthcare, or other critical personal information.
- Use a reputable password-protected open-source password manager such as BitWarden or KeePass to encrypt and store all of your user name and password records to minimize losing your log-in credentials. This way you only need to remember one master password to access all of your other passwords.
Click here to check how easy it is to crack your password with a computer.
Note that some web sites actually limit the allowable character set for password creation (e.g., no special characters), making it even more critical that you create strong passwords / pass-phrases.
The following list provides links to useful resources for learning more about the importance creating and using strong passwords:
1. How Big is Your Haystack, by Steve Gibson, is an excellent web page that explains how easy-to-remember yet strong passwords can be created, how real-world password strength is derived, and why many password “strength calculators” should not be relied upon.
2. Dan Wheeler’s 2012 blog post explains how password strength is derived, with comparison of strength of passwords as tested by different online password testing sites. Bitwarden.com has password strength test site based upon Dan Wheeler’s testing algorithm.
3. Your Password vs. a Supercomputer - this site measures the estimated elapsed time required to compute a brute-force hack of any given password based only on password length and characters/symbols to be used based computing power of a typical consumer computer and a supercomputer. All you need to enter isThe results can be alarming - it shows how quickly high powered computers can defeat most passwords in use today. The purpose of showing the results is to highlight the threat posed by attackers with access to multimillion dollar supercomputers as well as those equipped with affordable and widely available consumer GPU-assisted PCs and workstations.
4. PasswordMeter.com - this is one of the best overall password strength test pages online. This site will provide the estimated effectiveness of any given combination of alphanumeric characters and special symbols you might use to create a password. It shows results in real-time as you type based upon complexity and length. Unlike most other sites, this site show the variable parameters used to calculate the results.
5. Password complexity estimator - this site will give an approximation of long it would take for a hacker, using various brute-force methods, to crack the password you’ve entered.
6. Why you can’t trust password strength test meters - this site name says it all - every one of these sites uses different algorithms to calculate potential password strength and you will never obtains the the same results from any two sources.
